By Tamara Lev, Consultant, Tueoris, LLC.
Introduction
In today’s data-driven environment, businesses around the world consume vast amounts of personal information. Yet many of these businesses are unaware of where that high-value and often high-risk data is living within their organizations and out into their third-party ecosystems. Although the EU General Data Protection Regulation (“GDPR”) has impacted the global business market and has made companies more attentive to personal information, the new California Consumer Privacy Act (“CCPA”) appears set to drive further change for US domestic and international businesses alike.
As most professionals responsible for privacy and compliance are aware, the CCPA (which comes into effect in January of 2020) grants California consumers a number of new or enhanced rights. Amongst these are the right to know what personal information is being collected, whether it is sold or disclosed, and to whom. Further, California consumers can also now request access to and deletion of their personal information and affirmatively opt out of the sale of their personal information (a term which is defined broadly under the CCPA).
In order to effectively comply with these new legal obligations, businesses need to gain a robust understanding of where their personal information is being processed, shared and stored. By mapping the location and flow of personal information prior to January of 2020, companies can take a key step toward meeting the demands of California consumers and new CCPA obligations.
Data Mapping
Data mapping has become a popular term in recent years, often referring to the recording of the characteristics of a processing activity in order to meet GDPR Article 30 requirements. Rather than the creation of Article 30 Records of Processing, the data maps referred to here provide a visual depiction of the lifecycle of personal information through a defined process, including the applications, systems, databases and third parties to which the data flows. A successful data mapping initiative depicts the specific elements of personal information involved in the process. Accurate and well-constructed data maps become a highly valuable reference tool which can ultimately help the business meet its compliance obligations.
Mapping Personal Information to Meet CCPA Notice and Consent Requirements
Identification of the intake points for personal information enables the verification of and – if necessary – the implementation of appropriate privacy controls such as notice and consent. Under the CCPA, consumers must be informed of the categories of personal information being collected and the purposes for which it will be processed. Data intake for a particular processing activity may occur through various channels (e.g., website, email, third party lists) and it is important to accurately identify each intake point in order to effectively meet notice and consent requirements. In addition, because data maps frequently reveal secondary or tertiary downstream processing activities that may not be obvious to those individuals driving collection, but of which data subjects must be informed at the time of collection, the maps facilitate more robust and accurate privacy notices, resulting in a higher degree of compliance.
The CCPA requires businesses to obtain consent in certain instances, including transfers of personal information of minors to a third party. Companies processing personal information of California residents under the age of 16 have an affirmative obligation to obtain consent from that child or, when the personal information is being sold to third parties, from a parent or guardian. As such, mapping initiatives should focus on capturing not only the flow of the personal information, but also the characteristics of the data subjects, including identification of whether they are minors, as well as additional data elements which may trigger legal obligations under the CCPA or other applicable laws such as HIPAA, COPPA or international data protection laws.
Data Maps and Responding to Data Subject Requests
CCPA grants California consumers the right to know not only what information about them has been collected, processed and sold in the preceding twelve months, but also the source of that information. Identifying collection points and documenting these in data maps enables complete and compliant responses to access requests within the forty-five-day response window allowed by the CCPA.
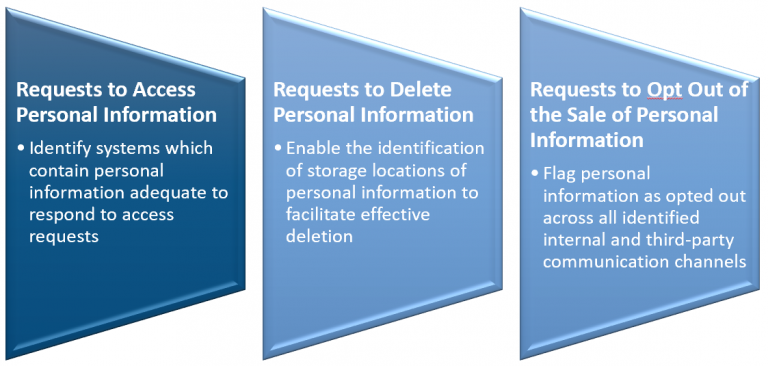
Of course, the source of the personal information is only one component of what must be provided to the California data subject. A business must also provide information regarding the third parties with which the company shares personal information. Data maps provide a readily available and understandable reference to ascertain that information in an efficient manner in order to respond to an access request.
Access requests are only one of a number of new CCPA requirements. The act also requires that California residents be provided a clear and unambiguous opportunity to opt out of the sale of their personal information to a third party (for example, a business collecting personal information online must clearly indicate the option to opt out by stating on its homepage: “Do Not Sell My Personal Information”). This is a critical component of the CCPA, because if opt out requests are not effectively resolved and consumers continue to receive unwanted communications from third parties, the first party business faces the risk of complaints, statutory fines, civil penalties and regulatory scrutiny. Thus, businesses need to identify the parties to which they are selling consumer personal information in order to instruct them regarding the opt out request. Data maps provide an optimal format for identifying these parties, one which readily understandable by business and IT staff who may be called on to respond to data subject requests.
The benefits of datamaps are clear when it comes to requests to delete personal information. Such requests simply cannot be fulfilled in a complete and effective manner unless the business is aware of where the requestor’s personal information is stored and the third parties with which it is shared. In today’s outsourced and cloud-based business environment, it is commonplace for data storage to take place outside of the four walls of the entity’s network and CCPA requires that a business in receipt of a deletion request also direct service providers to delete the consumer’s personal information from their records. Data maps should clearly indicate whether storage is on company owned assets or whether personal information resides with a third party or in a cloud environment. This information can then be leveraged to communicate the deletion requests to those third parties. Additionally, once the nature of the personal data storage is determined, it may be appropriate to seek assistance from legal and compliance colleagues to determine whether contractual terms are in place that will enable the fulfillment of deletion requests under the CCPA.
Naturally, if the data is no longer present within a company’s systems or with outsourced service providers, the response to a data subject request can be greatly simplified. Data retention and destruction policies and procedures are notoriously difficult to operationalize. However, documenting the process and timing for destruction of personal information (e.g., “applicant personal data is deleted from company systems after one year”) on data maps provides the business with a practical reference point to make an initial determination of whether the personal information still resides within its systems and environment.
Data Attributes and Security Controls
Data attributes comprise a critical component of a complete map that will support CCPA compliance efforts. The CCPA requires businesses to “implement and maintain reasonable security procedures and practices, appropriate to the nature of the information” to protect personal information from unauthorized disclosures. The design and implementation of reasonable security controls cannot be effectively accomplished without first understanding the nature of the data that must be secured. Data maps that capture and document the actual data elements being collected, transferred and stored become a highly valuable tool in determining the appropriate level of security necessary and identifying instances in which appropriate security may be lacking. Personal information with high-value or highly sensitive data attributes can be highlighted to inform security teams that they must consider applying greater safeguards. Likewise, such data going out to third parties or to less secure environments might require additional protections, such as encryption or pseudonymization. Privacy and security teams should remain aware that under the CCPA, civil actions may be brought against a business that fails to maintain reasonable security measures. The Act calls for penalties ranging from $100 to $750 per California resident, per incident, and in instances where the actual damages are greater than the statutory fines, actual damages will prevail. In addition, courts can award additional relief as they deem fit. And while risks from individual actions may appear reasonably manageable, risks from class actions are substantial and must be considered and mitigated.
Conclusion
Data maps that depict the collection, flow and processing of personal information through its lifecycle within identified processes, comprise a highly useful reference tool that enables effective compliance with CCPA requirements. A data map that depicts the information lifecycle at the appropriate level of depth is also a tool that the business, privacy and IT can all use to gain an accurate and consistent understanding of what is transpiring with personal information within their internal and third-party ecosystems. Of course, creating these maps can be a complex undertaking and requires the right IT and business stakeholders as well as team members who can take the information and translate that into readily understandable process flows. While a mapping initiative can be a significant undertaking, the payoff in terms of compliance, improved security and a common understanding amongst diverse teams, is well worth the effort.

0 Comments