Third-Party Risk Management (TPRM) is a key component of information security (infosec) programs and it requires significant focus. This is borne out by breaches in the news as well as known data on breaches reported to regulators.
For example, data on breaches at healthcare organizations reported last year shows that about 40% of the breaches involved a Business Associate1 (i.e. a third party to a healthcare provider or healthcare insurer).
What could we do to improve the performance and results of our TPRM programs?
This two-part article attempts to answer the question – the first part (this post) defines key objectives for TPRM programs followed by a discussion of common reasons why the programs often encounter challenges in meeting the objectives.
The second part to follow will include a discussion of certain ideas that can help the TPRM ecosystem (comprising of customers, their third parties, TPRM solution vendors etc.) in overcoming these challenges collectively.
Table of Contents
Key Factors/Objectives
In my view and experience, the success of a infosec TPRM program can be measured by three key overarching factors or objectives. These objectives are best understood in terms of outcomes or benefits they can deliver to customers and their third parties alike, as discussed below:
Effectiveness
- Customer – Can and does a customer’s TPRM program identify and actively manage relevant risks posed by a third party to the security of customer’s data, operations and indeed their overall business?
- Third Parties – Might a customer’s approach to TPRM be forcing their third parties to spend more and more of their limited time and resources on answering questionnaires or meeting other customer mandated requirements and (consequently) lesser time and resources on meaningful risk mitigation or management?
Agility/Scalability
- Customer – Can and does a customer’s TPRM program cover their ecosystem of third parties in a timely manner without compromising effectiveness (i.e. Objective #1)?
- Third Parties – Might a customer’s approach to TPRM be preventing their third parties from responding to the customer’s as well as other customers’ TPRM needs in a timely manner without compromising effectiveness of the customers’ TPRM programs?
Efficiency
Can and does the program meet the above two objectives in an efficient manner (i.e. at lower costs in time and resources) for customers as well as third parties?
The Continuing Challenge
While the three factors are necessarily straightforward to understand, driving commensurate results has been far from easy for most TPRM programs, in my view and experience. This is despite the considerable increase in availability of solutions or technologies at lower costs, which could or should have made it easier for TPRM programs to achieve the results.
So, why do many TPRM programs have challenges in achieving these objectives?
Reasons for underperformance
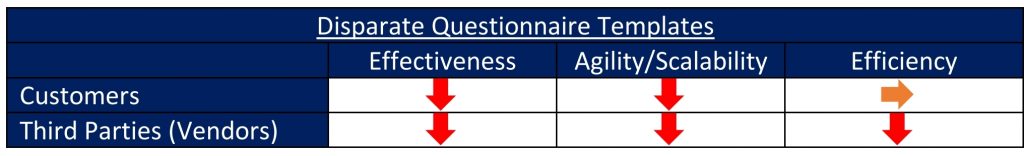
Disparate questionnaire templates
I have had the opportunity of seeing this problem up close, through our work in supporting TPRM initiatives or tasks both from the sending (customers) and receiving (vendors or third parties) parties’ standpoints. It is likely no secret to anyone who has been in a similar position that while some organizations choose to use better-known standard questionnaire templates (e.g. Shared Assessments’ SIG or SIG Lite), many organizations have adopted their own custom versions of questionnaires.
Use of disparate or custom questionnaire templates is usually burdensome to vendors or third parties for obvious reasons.
Effectiveness – Faced with limited resources and tight timelines, third parties often fill out the questionnaires with incomplete or inaccurate content. This does not serve the customer’s effectiveness objective well. The more the number of disparate questionnaires that a third party receives, the less time they are left with to spend on meaningful risk management operations. This results in reduced effectiveness of their risk management programs.
Agility/Scalability – If a customer receives incomplete or inaccurate responses to a questionnaire, they will likely need to have additional back-and-forth conversations with the third party. The more time (than necessary) that they spend on any one third party, the more likely the customer will find themselves short on time and resources to cover their remaining third parties that need their attention. One can tell how this would not serve the Agility/Scalability objective well for the customer or third-party.
Efficiency – The burden of having to deal with disparate questionnaires would very likely result in increased costs and (therefore)reduced efficiencies for third parties. As for customers, one could expect that using a standard questionnaire will help with enhanced efficiencies. However, given the negative impacts to effectiveness and agility/scalability objectives discussed above, customer may not quite realize improved efficiencies they might have come to expect.
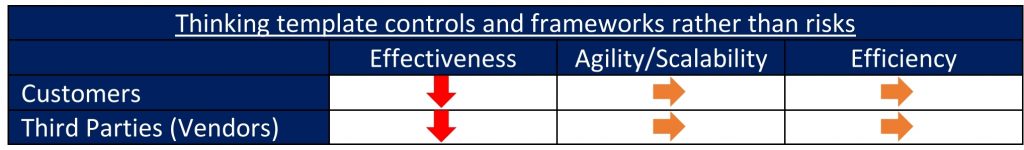
Thinking template controls and frameworks rather than risks
A significant part of questionnaires used by customers (whether through an online TPRM product exchange or offline mechanisms such as Excel) is based on a certain set of controls or a standard controls framework (such as ISO 27002, NIST 800-53 or HITRUST CSF).
Effectiveness – It is often hard to understand whether and how certain controls are truly risk-relevant individually or in entirety of the controls that are covered in the questionnaire. Risk relevance in this context refers to whether one can verifiably demonstrate that implementing the controls would decrease the likelihood of a security breach resulting from current or evolving security threats that may be applicable to the third-party’s environment and operations. Lack of a clear demonstration of risk relevance does not serve the effectiveness objective.
Agility/Scalability and Efficiency – Depending on the controls framework that is the basis for the questionnaire, the controls (and therefore the questionnaire or assessment) may also be too expansive or burdensome that it often runs counter to the agility/scalability and efficiency objectives.
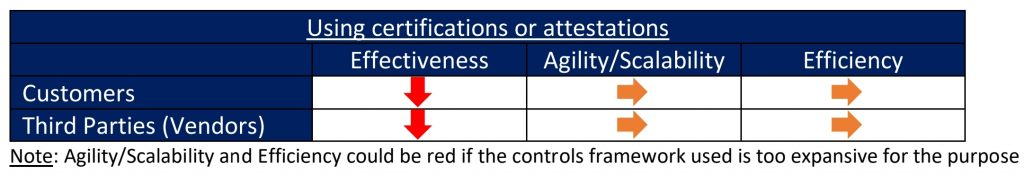
Using certifications or attestations
Customers often mandate or choose to rely solely or predominantly on attestations or certifications (e.g. SOC 2 Type 2, ISO 27001/2, HITRUST) for ascertaining risks posed by third parties. Such attestations or certifications may be the only choice for most customers if the third party in question is large and prominent such as one of the big public cloud providers. Since security is a critical business imperative to such large third parties and they usually carry multiple attestations or certifications at any point in time, it’s probably safe to rely on the attestations or certifications as the sole TPRM assurance mechanism.
However, one must be aware that such certifications may not provide the required levels of TPRM assurance for other third parties. Common reasons include:
- Insufficient demonstration of risk relevance. The certifying body does not verifiably demonstrate whether and how the security controls (prescribed by their controls framework) are effective against current and evolving security threats.
- Inaccurate or incomplete scoping or coverage. Controls scoping for certifications is performed using certain template factors defined by the certifying organization. Using such an “extraneous” set of factors may not be meaningful (i.e. fully risk relevant) in the specific context or the nature of services provided by the third-party to a particular customer. As a result, some of the controls used in a certification (of the third party) may not be as risk relevant to one or more customers depending on the nature and scope of the third-party’s services used by the customer.
- Inadequate assurance around operational capabilities. Certifications may be issued solely based on the third-party having security policies/procedures documentation and a certain level of implementation of the controls. Rarely do such certifications provide a level of assurance expected by customers in terms of whether and how the implemented controls are truly effective in day-to-day operations against likely security threats.
It is also pertinent to mention a couple of additional problems associated with certifications based on a predetermined set of controls:
- They are likely to force compliance or audit mindsets at the certified organizations instead of actively encouraging a focus on identifying new or evolving security risks and mitigating or managing them in a timely manner.
- Certain certification mandates may often result in diversion of a significant portion of (already) limited security budgets to such certification initiatives year after year. This would result in a perennial problem for these security programs in that they may not be left with necessary time or resources to pursue mitigation of certain known risks in a timely or effective fashion.
As such, certifications or attestations may not quite serve the effectiveness objective in most cases. Customers will have to resort to secondary means (such as additional walkthroughs or questionnaires) in order to obtain the level of assurance they need.
TPRM solutions and their implementation
A number of vendors have solutions that address TPRM needs of infosec programs. In fact, Gartner’s most recent “Critical Capabilities for IT Vendor Risk Management Tools report”2 includes as many as 23 vendors.
While these vendors solutions support TPRM needs to varying extent, most of their solutions use approaches that are fundamentally same or similar – assessments based on surveys or questionnaire built from standard security controls frameworks. Beyond this and certain other product features that may or may not be unique to each vendor solution, some vendors may offer managed services to TPRM programs while some also offer “assessment exchanges” that allow for vendors to share their completed assessments with other customers that may be on the same exchange.
As one would expect, some vendors are better than others in terms of how well their solutions and additional capabilities (such as services and exchanges) could help meet the three objectives of Effectiveness, Agility/Scalability and Efficiency for customers as well as their third parties. It is my view that some of the newer vendors have better capabilities in helping meet the three objectives than some of the vendors whose solutions might have been originally designed for meeting internal security Governance, Risk Management and Compliance (GRC) needs.
Regardless of how good a vendor solution may be in itself, a significant part of how well the solution meets the three objectives is dependent on each TPRM program – specifically, how well is a vendor solution or service leveraged as part of the customer or third party’s day-to-day operations. It is my view that many organizations need significant work to do in this regard.
Exchanges and Network Effect
The assessment exchanges (“exchanges”) mentioned in the previous section are run by TPRM solution vendors and therefore are useful only for those customer and third-party organizations that use the particular vendor’s solution or service. While some customers may be able to use just one solution vendor, third parties are usually forced to adopt vendor solution(s) or exchanges that each of their customers may be using.
Further, different vendor-run exchanges are not interoperable in the sense that assessment content on one exchange can’t be readily accessed or transferred by participants in another exchange.
As a result, the exchanges’ potential for “network effect” is curtailed and the Agility/Scalability and Efficiency benefits do not meet one’s expectations.
………………….
A following post will discuss ideas for how the TPRM ecosystem (comprising of customers, their third parties, TPRM solution vendors etc.) might overcome these challenges collectively.
Reference:
1. Breaches of unsecured protected health information affecting 500 or more individuals reported to U.S. Department of Health and Human Services, Office for Civil Rights
https://ocrportal.hhs.gov/ocr/breach/breach_report.jsf
2. Critical Capabilities for IT Vendor Risk Management Tools, Published: 24 August 2020

0 Comments