By Dan Goldstein, Co-Founder and Partner, Tueoris, LLC.
Introduction
If you’re a privacy professional that spent a good chunk of 2018 living through the run-up to the EU General Data Protection Regulation (GDPR), 2019 is set to have a somewhat familiar feel. This year though, the requirements driving a flurry of privacy compliance activities will be largely driven by US state law. As most professionals responsible for privacy and compliance are aware, the California Consumer Privacy Act (“CCPA”) will come into effect in January of 2020, granting California consumers a number of new or enhanced rights. While there has been plenty of painstaking analysis of the provisions of the Act and how they apply to data subjects and businesses, far less has been written about how covered businesses can practically meet their CCPA obligations.
If your business falls within the scope of the CCPA, one of the most significant requirements will be responding – and being prepared to respond – to requests from California consumers to access their personal information, have their personal information deleted from your systems (and those third parties to which you have sold the data) and to opt out of the sale of their personal information. All of which begs the question, how can businesses that have not had these obligations in the past get prepared to respond to such requests beginning in 2020?
Ascertaining Where Personal Information Resides
In order to effectively comply with new CCPA obligations, businesses need to ascertain where personal information is located, as well as how it is being processed, shared and stored. Businesses falling within the CCPA’s scope should consider undertaking a data mapping exercise to gain such an understanding.
Data mapping has become a popular term in recent years, often referring to the recording of the characteristics of a processing activity in order to meet GDPR Article 30 requirements. These records of processing are commonly created with automated tools or manually with a spreadsheet, but in each case, the output is generally a table detailing the processing activity. Alternatively, data maps can provide a visual depiction of the lifecycle of personal information through a defined process, including the applications, systems, databases and third parties to which the data flows. Each approach has its benefits and limitations, but either can be leveraged to meet compliance obligations under the CCPA.
Regardless of the approach taken, an accurate and detailed understanding of the collection points, sources, storage and third-party sharing of personal information is critical in responding to consumer requests under the CCPA. In addition, because mapping exercises frequently reveal secondary or tertiary downstream processing activities that may not be obvious to those individuals driving collection, but of which consumers must be informed at the time of collection, the maps facilitate more robust and accurate privacy notices.
Fulfilling Consumer Requests with Response Process Workflows
Gaining an understanding of the lifecycle of personal information through a mapping exercise is a critical component of CCPA compliance, but alone, it doesn’t provide an operational solution to meeting consumer requests under the Act. Effectively meeting such requests in a consistent manner requires a templatized and repeatable approach that avoids stakeholders spending hours trying to solve the puzzle of what personal information must be produced, deleted or blocked, and determining all data stores where such information resides.
The solution to this truly complex operational problem is the creation of documented visual process workflows – one for each type of request – that provide highly detailed yet easy to follow guides to fulfilling requests. Such workflows, produced in a thorough and accurate manner, provide those charged with fulfilling consumer requests under the CCPA with a single and complete source of the information they need to satisfy their obligations. In order to produce truly usable workflows, stakeholders from the business and IT sides of the house must have a seat at the table.
These process workflows are built on the basis of the “functional requirements” of CCPA compliance. This refers to the functionalities that must exist within the process in order to lawfully and effectively respond to a consumer request. For example, an obvious functional requirement of the CCPA is that a California consumer must have a mechanism by which to make a request. This may be depicted in the process flow, (depending on the nature of business), as something as simple as a dedicated email address or as sophisticated as a carefully tailored self-service portal. Other functional requirements might be driven out by well-established data security principles, such as verification of a requestor’s identity prior to providing personal information in response to a request. The process workflows reflect operational “solutions” to functional requirements throughout the process.
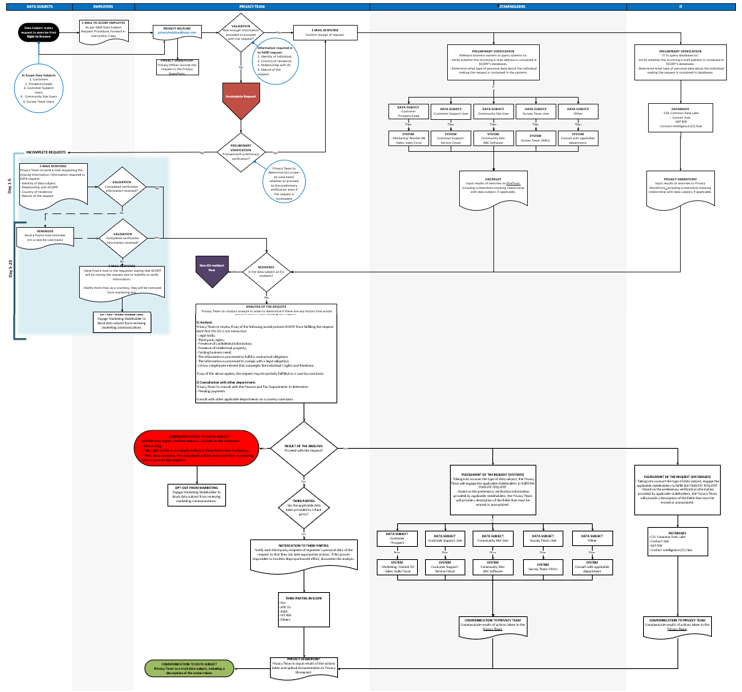
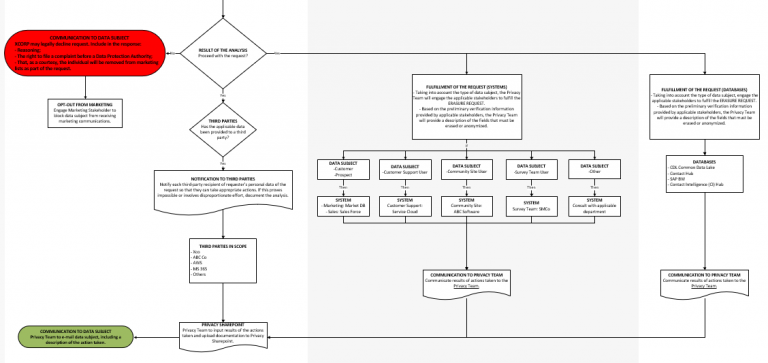
The workflows leverage the information gathered in the data mapping exercises so that each process flow contains the specific sources, data stores and third parties involved in order to effectively respond to a request. For example, a California consumer making an access request has the right to know not only what personal information is being processed, but also the source of that information. The team tasked with design and development of the workflow for an access request will leverage the data maps (or data mapping tables) to create workflows which identify the specific intake points (data sources) which need to be disclosed, as well as the relevant data stores (both internal and external/cloud based) to accurately report the specific data elements being processed. CCPA also allows a consumer to request information about the category of third parties with which the company shares personal information. Common or established third-party transfers will also be carried over from the data maps and reflected in the workflows to create a resource that facilitates complete and accurate responses to access requests.
Because the required activities and in-scope data, sources and stores may differ according to the type of request, individual process workflows should be created for access, deletion and requests to opt out from sales of personal information. Businesses may also process personal information of sufficiently distinct groups of consumers that require different workflows due to the unique characteristics of the processing (e.g., the systems and data stores for employee personal information may be distinct from systems and data stores for customer or prospects).
Conclusion
The creation of detailed process workflows, leveraging a thorough and accurate data mapping exercise, will facilitate the ability to respond to consumer requests in a thorough and compliant manner. Absent a thorough and repeatable process to respond to consumer requests, businesses impacted by the CCPA will be at risk not only of regulatory scrutiny, fines and reputational damage as privacy continues to gain more and more visibility with US consumers. While nearly a year appears to be more than adequate time to ramp up CCPA compliance mechanisms, planning should be undertaken soon, allowing time for training, dry runs and improvements to process workflows prior to January of 2020.

0 Comments