If you didn’t notice already, the Office of Inspector General (OIG) in the Department of Health and Human Services (HHS) published a report on the oversight by the Center for Medicare and Medicaid Services (CMS) in the enforcement of the HIPAA Security Rule. The report is available to the public here. As we know, CMS was responsible for enforcement of the HIPAA Security Rule until the HHS Secretary transferred that responsibility over to the Office of Civil Rights (OCR) back in 2009.
To quote from the report, the OIG conducted audits at seven covered entities (hospitals) in California, Georgia, Illinois, Massachusetts, Missouri, New York, and Texas in addition to an audit of CMS oversight and enforcement actions. These audits focused primarily on the hospitals’ implementation of the following:
- The wireless electronic communications network or security measures the security management staff implemented in its computerized information systems (technical safeguards);
- The physical access to electronic information systems and the facilities in which they are housed (physical safeguards); and,
- The policies and procedures developed and implemented for the security measures to protect the confidentiality, integrity, and availability of ePHI (administrative safeguards).
These audits were spread over three years (2008, 2009 and 2010) with the last couple of audits happening in March 2010. The report doesn’t mention the criteria by which these hospitals were selected for audit except that these hospitals were not selected because they had a breach of Protected Health Information(PHI) .
It wouldn’t necessarily be wise to extrapolate the findings in the report to the larger healthcare space in general without knowing how these hospitals were selected for audit. All one can say is that the findings would paint a worrisome picture if these hospitals were selected truly in a random manner. For example, if one were to look at ”High Impact” causing technical vulnerabilities, all 7 audited hospitals seem to have had vulnerabilities related to Access and Integrity Controls, 5 out of 7 had vulnerabilities related to Wireless and Audit Controls and 4 out 7 had vulnerabilities related to Authentication and Transmission Security Controls.
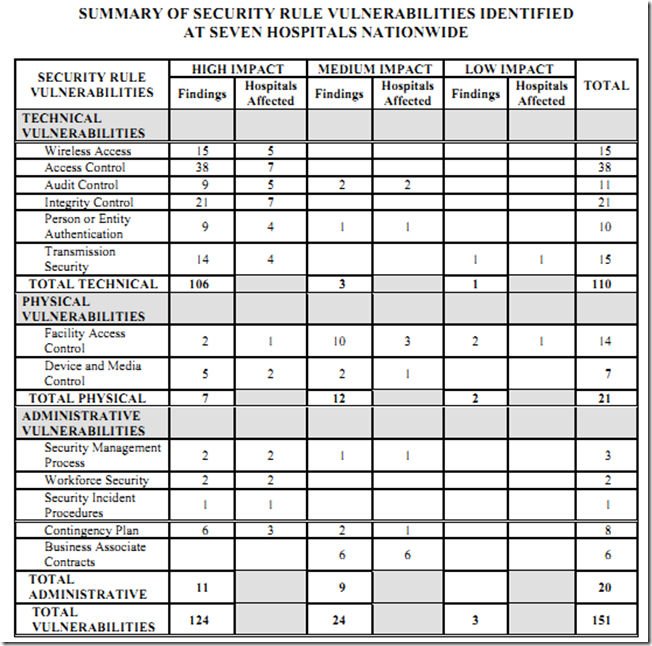
What might be particularly concerning is that the highest number of vulnerabilities were in the Access and Integrity Controls categories. These are typically the vulnerabilities that are exploited most by hackers as evidenced (for instance) by the highlight in this quote from the 2011 Verizon Data Breach Investigation Report – “The top three threat action categories were Hacking, Malware, and Social. The most common types of hacking actions used were the use of stolen login credentials, exploiting backdoors, and man-in-the-middle attacks”.
Wake-up call or not, healthcare entities should perhaps take a cue from these findings and look to implement robust security and privacy controls. A diligent effort should help protect organizations from the well publicized consequences of a potential data breach.

0 Comments