Health Information Security/Privacy professionals should be familiar with the HIPAA Breach Notification Rule, which requires HIPAA covered entities (CEs) and their business associates (BAs) to provide notification to U.S. Department of Health and Human Services Office for Civil Rights (OCR) following a breach of unsecured protected health information (PHI).
CEs and BAs submit their notifications using the OCR Breach Portal. Details of the information required to be included in each submission are available in this document.
We reviewed the breach notifications submitted between January 1st 2020 and December 31st 2020. This post includes our observations and recommendations based on the data that is publicly available in the portal.
Table of Contents
Data and Context
The tables below show a summary of breaches reported in 2020.
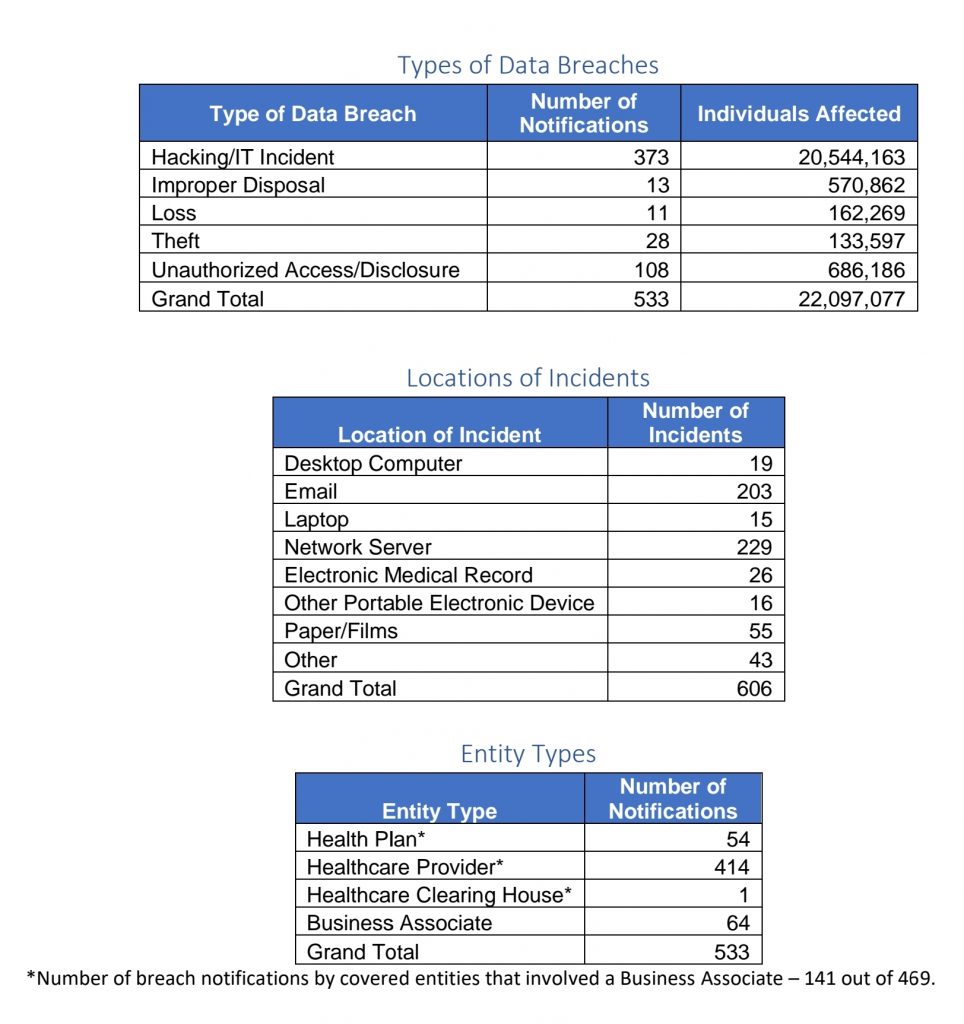
It’s worth providing some context to these aggregate numbers, due to who (CE or BA) reports the breaches to OCR and when they are reported.
- Notifications may not mean the same as incidents that led to the breaches. The number of notifications shouldn’t be confused with the number of unique incidents that led to the breaches. A breach that occurred at a BA might be reported by multiple CEs that were affected by the breach. Each CE submission appears as one notification. For example, a prominent ransomware incident in 2020 impacted several CEs and many of the CEs provided the notifications as one can see from the data available in the portal.
- Not all of the breaches would have actually occurred in 2020. This is because the HIPAA Breach Notification Rule allows up to 60 days after discovery for notification of a breach that involved more than 500 records of PHI. For breaches that involved less than 500 records, a CE or BA has up to 60 days after end of the calendar year in which the breach was discovered. It is likely that several of these notifications pertained to breaches that actually occurred in 2019 or even earlier considering that some breaches are discovered months after the initial exploit occurred.
It is also useful to note the following observations regarding the data available through the portal:
Limited Publicly Viewable Information
Information available for public viewing on the breach portal is fairly limited. This limits the quality and quantity of analysis one can perform and draw lessons from.
Breaches involving less than 500 records are not posted
None of the listed notifications pertain to breaches involving less than 500 records. It is not clear why – whether there have not been any breaches involving less than 500 records or OCR has decided not to make them available for public viewing.
Observations
Most breaches result from information security incidents of electronic nature (as opposed to physical loss or theft).
The data on types of breaches shows that a majority of the notifications resulted from hacking or IT incidents. Data on the nature and types of these incidents is not available on the portal.
However, limited research of the published accounts of the incidents indicates that a significant number of these incidents resulted from ransomware and compromise or breach of email systems or accounts.
Unauthorized Access or Disclosure is still prominent.
These breaches form the second largest category. Based on limited research over the internet, these incidents usually range from unauthorized insider access to PHI as well as unintentional exposure of PHI due to an error of some nature.
Incidents resulting from deficiencies in physical security or secure disposal have been on the decrease.
Incidents of physical theft, loss or improper disposal of paper or media containing PHI likely belong to this category. This category used to account for the highest number of breaches a few years ago as evident from one of our past blog posts but has been surpassed by hacking and unauthorized access/disclosure categories in the recent years.
Third parties (BAs) are responsible for a significant number of breaches.
A total of 64 out of 533 breaches were reported by BAs. Additionally, another 141 breaches reported by CEs involved BAs.
In aggregate, BAs were responsible for as many as 205 of the 533 breaches reported in 2020.
Email is a significant breach vector.
One in three breaches involved email compromise.
It goes to show that improving email security alone could yield healthcare significant returns in breach avoidance.
Recommendations
Given the observations above, we suggest the following risk mitigation steps for healthcare organizations to reduce the likelihood of them getting breached and having to notify regulators:
Implement effective ransomware safeguards.
Ransomware appears to have been one of the leading causes of the breaches reported last year. US Cybersecurity Infrastructure Security Agency (CISA) has been issuing timely and useful advisories regarding ransomware targeted on Healthcare organizations, such as this advisory.
These advisories also contain useful safeguards organizations can implement to prevent or contain ransomware incidents.
We would recommend healthcare organizations use this guide to assess their ransomware readiness periodically.
Design and implement a formal program for unstructured data protection.
Proliferation of PHI in unstructured form (i.e. outside of Electronic Health Records systems or EHRs, clinical or other authorized applications, databases etc.) usually poses significant risk that leads to breaches. In the absence of a good inventory (of the locations such data might be, who might be using the data (if at all) and what might it be used for etc.), it is nearly impossible to implement appropriate safeguards to protect the data. Such unstructured data is often found in emails, user endpoints, file servers etc.
We would recommend organizations implement formal initiatives for unstructured data protection – with a key objective of minimizing such data and consolidating data repositories into centralized systems or applications that allow for design and enforcement of improved preventative and detection capabilities.
Improve email security.
One might consider several steps to improve email security.
These include:
- Avoid use of email for storage or transmission of PHI as far as possible
- Use centralized repositories or secure collaboration or file sharing applications for storage and sharing of PHI in unstructured form outside of clinical applications, EHRs or other business applications or databases that are authorized to store or process PHI. Such centralized repositories must implement the following safeguards:
- Risk based stronger authentication
- Least Privilege access controls (authorization/entitlements)
- Monitoring for anomalous or potentially unauthorized use of the data
- Encryption of data at rest and when accessed
- Anti-spam and phishing safeguards
- User awareness and training
Operationalize effective detection and response.
Early or timely detection can help contain or prevent security incidents or exploits from turning into reportable breaches. This requires thoughtful implementation and operationalization of detection and response technologies and programs.
Effective and timely detection and response has been a challenge not just in healthcare but also other industries as evidenced by published reports[1]. It is common to find organizations implementing necessary technologies and yet not realize expected outcomes in detection for prolonged periods of time.
Effective implementation and operations of detection technologies should help avoid breaches in most of the locations they occur as noted in the “Locations of Incidents” table above – including desktops/laptops, email, network servers and EHR or other applications that process PHI.
As an example from our blog, this post covered how a prominent breach at a healthcare payor could have been detected and perhaps stopped.
Implement pragmatic Third Party Risk Management (TPRM)
Effective TPRM programs can help mitigate risks posed by BAs.
When a security breach at a BA impacts several CEs at the same time as seen from reported notifications, it is worth asking why is that none of the CEs’ TPRM programs could help avoid the breach.
We think this problem can be addressed through a conscious choice of TPRM approaches or practices that deliver best results not only CEs but also BAs. We discussed this in detail recently.
Suggestion for OCR
Last but not the least, we think it would be immensely useful if OCR could provide additional insights regarding these breaches (perhaps through their annual reports to Congress or otherwise), without having to disclose identities of the breached organizations.
For example:
- Who were the threat actors?
- How long did the average breach last?
- How long did it take to discover breaches on an average?
- How were the breaches detected?
- Specifics regarding breaches associated with network servers (it being too broad a category)
- What types of clinical or other applications were breached?
- What elements of PHI were part of the breach?
- Which security safeguards worked, and which didn’t?
- What actions were taken in response to breaches?
Such insights could help healthcare organizations in finetuning their focus and investments on those safeguards and tasks that can best help them avoid breaches.
[1] FireEye Mandiant M-Trends 2020 Report, 2020 CrowdStrike Services Report, IBM – Cost of a Data Breach Report

0 Comments