Information security (infosec) risk management can often seem overwhelming and hard. Organizations can spend considerable resources on infosec programs or solutions, yet they may have challenges in implementing commensurate and demonstrable …
COMPLIANCE
Operationalizing CCPA Compliance: Know Your Data and Establish Detailed and Practical Workflows
By Dan Goldstein, Co-Founder and Partner, Tueoris, LLC. Introduction If you’re a privacy professional that spent a good chunk of 2018 living through the run-up to the EU General Data …
EU Privacy and US Trade Limitations: Opening New Opportunities for Mexican Business
By Mayra Cavazos, Senior Consultant, Tueoris, LLC Introduction The European Union (EU) General Data Protection Regulation (GDPR) has impacted businesses around the world in a variety of different ways, influenced …
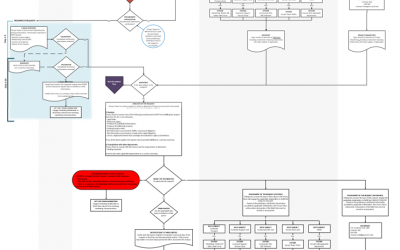
Driving Effective Privacy Operations with Functional Requirements
By Shawna Doran, Senior Manager, Tueoris, LLC and Dan Goldstein, Partner, Tueoris LLC In the run-up to May 25, 2018, many businesses that thought they were well-prepared to meet their …
Alternatives to Consent: New Approaches to Processing Patient Data for Current and Future Clinical Research
Introduction Pharmaceutical and biotech companies sponsoring clinical research have traditionally relied on patient consent as the legal basis for processing personal data, sensitive personal data and biologic material for …
Is your auditor or consultant anything like the OPM OIG?
The OPM breach has been deservedly in the news for over a month now. Much has been written and said about it across the mainstream media and the internet1. …
Patient Portals Make or Break
Like many other Health IT initiatives today, the primary driver for patient portals is regulatory in nature. Specifically, it is the Meaningful Use requirements related to view, download or transmit and …
Hello PCI SSC… Can we rethink?
This is a detailed follow-up to the quick post I wrote the Friday before the Labor Day weekend, based on my read at the time of the PCI SSC’s Special Interest Group …
Security is mostly basics, but talk is cheap
In most cases, better security posture is all about getting a few basics right. And this recent incident related to the breach of a Healthcare.gov server may be further proof …