Like many other Health IT initiatives today, the primary driver for patient portals is regulatory in nature. Specifically, it is the Meaningful Use requirements related to view, download or transmit and secure messaging. However, the biggest long term benefit of the portals might be what they can do for patient engagement and as a result, to the providers’ business in the increasingly competitive and complex healthcare marketplace in the United States.
The objective of this post is to discuss the security aspects of patient portals, specifically, why the current practices in implementing these portals could pose a big problem for many providers. More importantly, we’ll discuss specific recommendations for due diligence actions that the providers should take immediately as well as in the longer term.
Before we get to discuss the security aspects, I think it is important to “set the stage” by discussing some background on patient portals. Accordingly, this post covers the following areas in the indicated sequence:
- What are patient portals and what features do they (or could) provide?
- Importance of patient engagement and the role of patient portals in patient engagement
- The problem with the current state in Health IT and hence the risks that the portals bring
- Why relying on regulations or vendors is a recipe for certain failure?
- What can/should we do (right now and in the future) – Our recommendations
What are Patient Portals and what features do they (or could) provide?
I would draw on information from the ONC site for this section. Here is the pertinent content, to quote from the ONC site:
A patient portal is a secure online website that gives patients convenient 24-hour access to personal health information from anywhere with an Internet connection. Using a secure username and password, patients can view health information such as:Some patient portals also allow patients to:
- Recent doctor visits
- Discharge summaries
- Medications
- Immunizations
- Allergies
- Lab results
- Exchange secure e-mail with their health care teams
- Request prescription refills
- Schedule non-urgent appointments
- Check benefits and coverage
- Update contact information
- Make payments
- Download and complete forms
- View educational materials
The bottom-line is that patient portals provide means for patients to access or post sensitive health or payment information. In the future, their use could expand further to include integration with mobile health applications (mHealth) and wearables. Last week’s news from EPIC should provide a sense for things to come.
Importance of patient engagement and the role of patient portals in patient engagement
As we said above, the primary driver for patient portals so far has been the Meaningful Use requirements related to view, download or transmit and secure messaging. However, the biggest long term benefit of the portals might be what they can do for patient engagement and becoming a key business enabler for providers.
The portals are indeed a leading way for providers to engage with patients, as can be seen in this graphic from the 2014 Healthcare IT Priorities published by InformationWeek1.
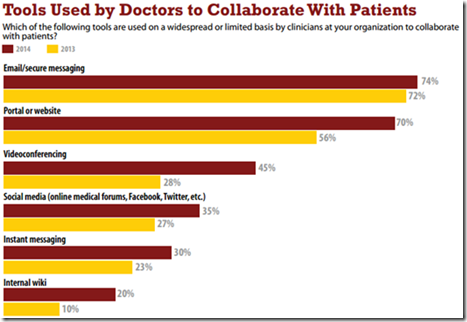
Effective patient engagement of course can bring tremendous business benefits, efficiencies and competitive edge to providers.
From a patient’s perspective, the portals can offer a easier method for interacting with their providers which in turn has its own benefits for patients. To quote from the recently released HIMSS report titled “The State of Patient Engagement and Health IT”2
A patient’s greater engagement in health care contributes to improved health outcomes, and information technologies can support engagement.
In essence, the importance of patient portals as a strategic business and technology solution for healthcare providers doesn’t need too much emphasis.
The problem with the current state in Health IT and hence the risks that the portals bring
In my view, the below quote from the cover page of the 2014 Healthcare IT Priorities Report published by InformationWeek1 pretty much sums it up for this section.
Regulatory requirements have gone from high priority to the only priority for healthcare IT.
We all know what happens when security or privacy programs are built and operated purely to meet regulatory or compliance objectives. It is a shaky ground at best. We talked about it in one of our blog posts last year when we called for a change in tone and approaches to healthcare security and privacy.
Why relying on regulators or vendors is a recipe for certain failure of your security program?
It is probably safe to say that security in design and implementation is perhaps not the uppermost concern that HealthIT vendors have (certainly not the patient portal vendors in my opinion) today. To make it easy for them, we have lackluster security/privacy requirements in the regulation for certifying Electronic Health Records.
Consider the security and privacy requirements (yellow in this pdf) that vendors have to meet in order to obtain EHR certification today. You will see that the certification criteria are nearly not enough to assure the products are indeed secure enough before the vendors can start selling them to providers. And then, the administration or enforcement of the EHR certification program has been lacking as well in the past.
If you consider a risk relevant set of controls such as the Critical Security Controls for Effective Cyber Defense, you will see that the certification criteria are missing the following key requirements in order to be effective in today’s security threat landscape:
- Vulnerability assessments and remediation
- Application Security Testing (Including Static and Dynamic Testing)
- Security training for developers
- Penetration tests and remediation
- Strong Authentication
Think about using these applications to run your patient portals!
If you are a diligent provider, you will want to make sure that the vendor has met the above requirements even though the certification criteria do not include them. The reality though may be different. In my experience, providers often do not perform all the necessary due diligence before purchasing the products.
And then, when providers implement these products and attest to Meaningful Use, they are expected to do a security risk analysis (see the green highlighted requirement in the pdf). In my experience again, risk analysis is not performed in all cases. Of those that perform them, many are not really risk assessments.
The bottom-line? … Many providers take huge risks in going live with their patient portals that are neither secure nor compliant (Not compliant because they didn’t perform a true risk analysis and mitigate the risks appropriately).
If you look again (in 1 above) at the types of information patient portals handle, it is not far-fetched to say that many providers may have security breaches waiting to happen. It is even possible that some have already been breached but they don’t know yet.
Considering that patient portals are often gateways to the more lucrative (from a hacker’s standpoint) EHR systems, intruders may be taking their time to escalate their privileges and move laterally to other systems once they have a foothold in the patient portals. Considering that detecting intrusions is very often the achilles heel of even the most well-funded and sophisticated organizations, it should be a cause for concern at many providers.
What can/should we do (right now and in the future) – Our recommendations
It is time to talk about what really matters and some tangible next steps …
What can or must we do immediately and in the future?
Below are our recommendations for immediate action:
- If you didn’t do the due diligence during procurement of your patient portal product, you may want to ask the vendor for the following:
- Application security testing (static and dynamic) and remediation reports of the product version you are using
- Penetration testing results and remediation status
- If the portal doesn’t provide risk based strong (or adaptive) authentication for patient and provider access, you may insist on the vendor committing to include that as a feature in the next release.
- If you didn’t perform a true security risk analysis (assessment), please perform one immediately. Watch out for the pitfalls as you plan and perform the risk assessment. Make sure the risk assessment includes (among other things) running your own vulnerability scans and penetration tests both at network and application layers.
- Make sure you have a prioritized plan to mitigate the discovered risks and of course, follow through and execute the plan in a timely manner.
Once you get through the immediate action steps above, we recommend the below action items to be included in your security program for the longer term:
- Implement appropriate due diligence security measures in your procurement process or vendor management program.
- Have your patient portal vendor provide you the detailed test results of the security requirements (highlighted yellow in the attachment) from the EHR certifying body. You may like to start here (Excel download from ONC) for information on the current certification status of your patient portal vendors and the requirements they are certified for.
- Ask the vendor for application security (static and dynamic) and pen test results for every release.
- Segment the patient portal appropriately from the rest of your environment (also a foundational prerequisite for PCI DSS scope reduction if you are processing payments with credit/debit cards).
- Perform your own external/internal pen tests every year and scans every quarter (Note : If you are processing payments with your payment portal, the portal is likely in scope for PCI DSS. PCI DSS requires you to do this anyway).
- Conduct security risk assessments every year or upon a major change (This also happens to be a compliance requirement from three different regulations that will apply to the patient portal – HIPAA Security Rule, Meaningful Use and PCI DSS, if processing payments using credit/debit cards).
- If you use any open source modules either by yourself or within the vendor product, make sure to apply timely patches on them as they are released.
- Make sure all open source binaries are security tested before they are used to begin with.
- If the vendor can’t provide support for strong authentication, look at your own options for proving risk based authentication to consumers. In the meanwhile, review your password (including password creation, reset steps etc.) to make sure they are not too burdensome on consumers and yet are secure enough.
- Another recommended option is to allow users to authenticate using an external identity (e.g. Google, Facebook etc. using OpenID Connect or similar mechanisms) which may actually be preferable from the user’s standpoint as they don’t have to remember a separate log-in credential for access to the portal. Just make sure to strongly recommend that they use 2 step verification that almost all of these social media sites provide today.
- Implement robust logging and monitoring in the patient portal environment (Hint : Logging and Monitoring is not necessarily about implementing just a “fancy” technology solution. There is more to it that we’ll cover in a future post)
In summary, there is just too much at stake for providers and patients alike to let the status quo of security in patient portals continue the way it is. We recommend all providers take priority action considering the lasting and serious business consequences that could result from a potential breach.
As always, we welcome your thoughts, comments or critique. Please post them below.
References
1 2014 Healthcare IT Priorities published by InformationWeek
2 The State of Patient Engagement and Health IT(pdf download)
Recommended further reading
Patient engagement – The holy grail of meaningful use
Patient portal mandate triggers anxiety
MU Stage 2 sparks patient portal market

0 Comments